Academic Research on Bitcoin Economic Security and Network Performance
A chronological selection of papers
Majority is not Enough: Bitcoin Mining is Vulnerable (Published in 2013)
Key passage: “We also show that at least 2/3 of the network needs to be honest to thwart selfish mining; a simple majority is not enough.”
Link to paper: https://www.cs.cornell.edu/~ie53/publications/btcProcFC.pdf
Picture of abstract:
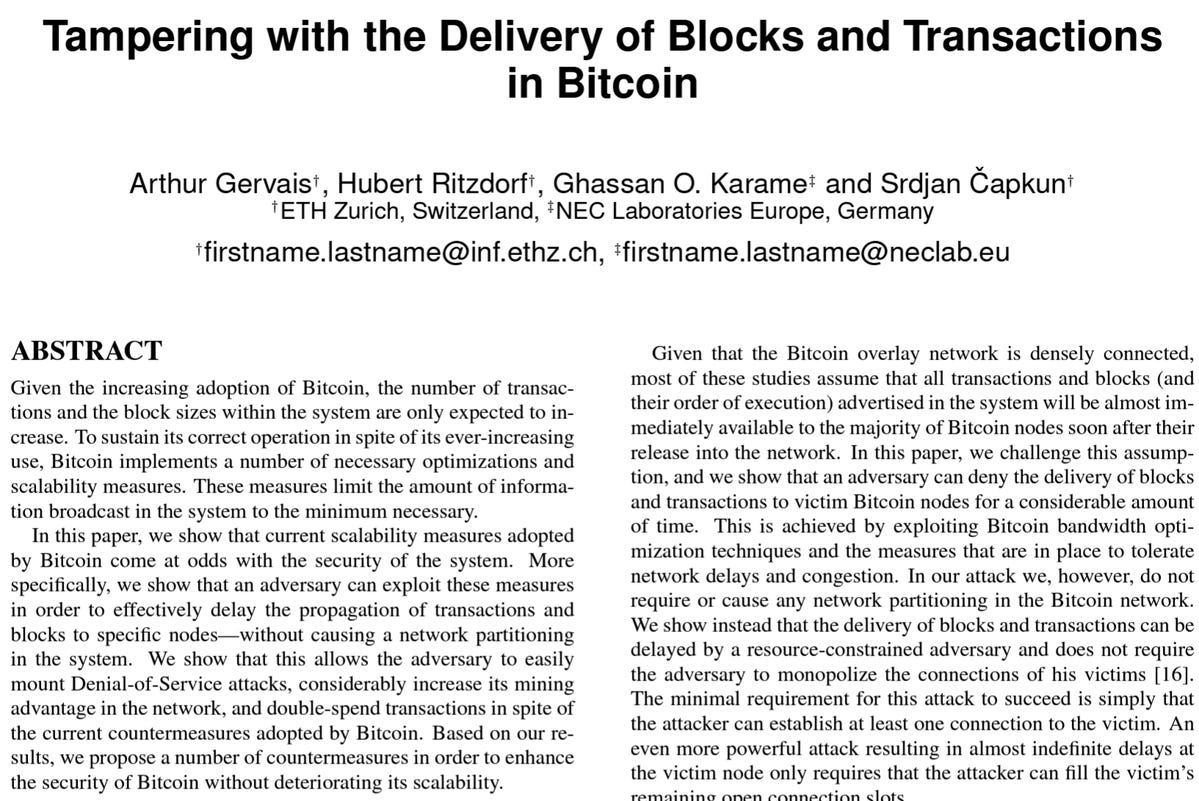
Tampering with the Delivery of Blocks and Transactions in Bitcoin (2015)
Key passage: “This adversary effectively controls the Bitcoin mining network given only 35% of the actual computing power.”
Link to paper: https://eprint.iacr.org/2015/578.pdf
Picture of abstract:
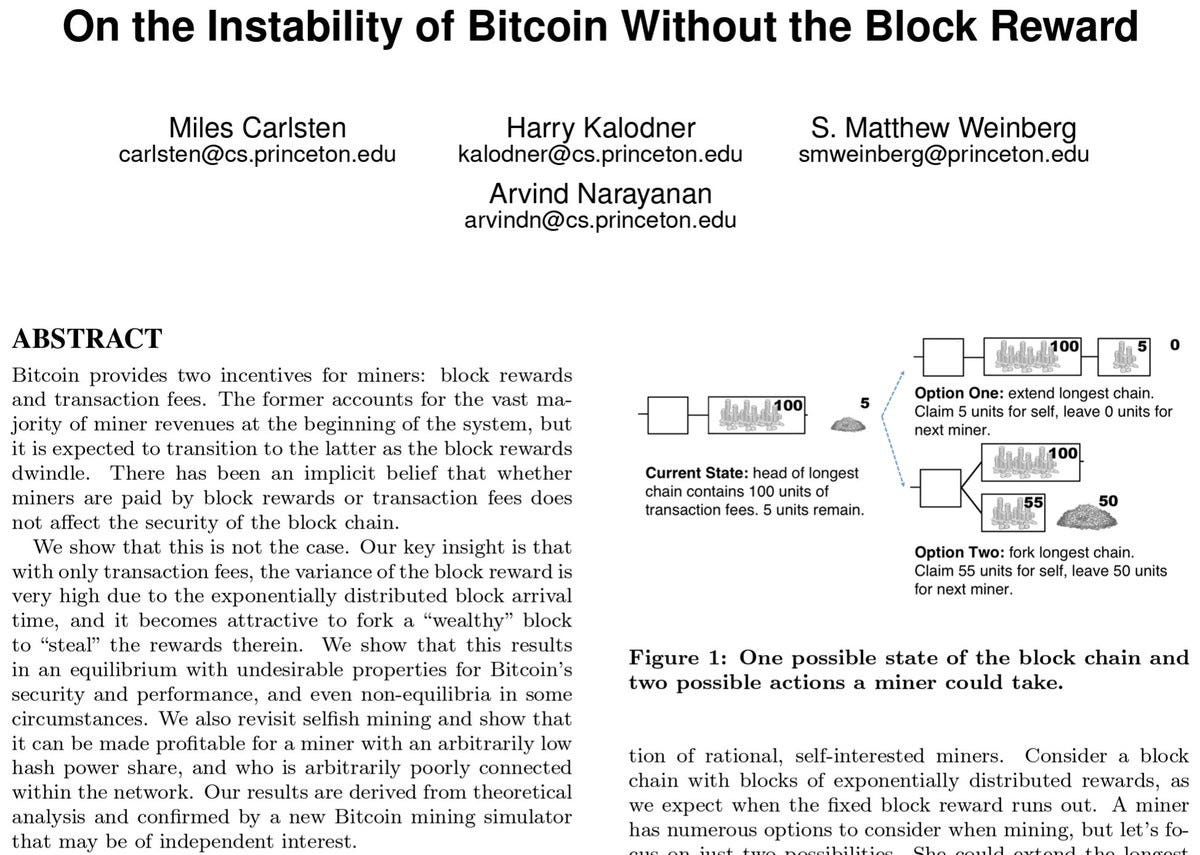
On the Instability of Bitcoin Without the Block Reward (2016)
Key passage: “the time-varying nature of transaction fees allows for a richer set of strategic deviations that don’t arise in the block-reward model”
Link to paper: https://www.cs.princeton.edu/~smattw/CKWN-CCS16.pdf
Video of talk:
Picture of abstract:
Bitcoin: A Natural Oligopoly (2018)
Key passage: “proof of work protocols result in high concentration of mining power in the presence of even minor cost asymmetries or economies of scale”
Link to paper: https://arxiv.org/pdf/1811.08572.pdf
Picture of abstract:
The Gape Game (2018)
Key passage: “…in about ten years…the system will be in a state where gaps are profitable.”
Paper link: https://arxiv.org/pdf/1805.05288.pdf
Video link:
Picture of abstract:
The Economic Limits of Bitcoin and the Blockchain (2018)
Key passage: “the blockchain is vulnerable to sabotage, and at a cost that is linear in the amount of specialized computational equipment devoted to its maintenance”
Link to paper: https://faculty.chicagobooth.edu/eric.budish/research/Economic-Limits-Bitcoin-Blockchain.pdf
Picture of abstract:
Hostile blockchain takeovers (2019)
Key passage: “…eliminating a competing system might increase the value of a surviving system” (2019)
Link to paper: https://fc18.ifca.ai/bitcoin/papers/bitcoin18-final17.pdf
Link to video:
Picture of abstract:
Explore the Attack Surface of Blockchain: A Systematic Overview (2019)
Summary: A review of blockchain security theory and significant historical incidents.
Paper: https://arxiv.org/pdf/1904.03487.pdf
Picture of abstract:
Selfish Mining Re-Examined (2020)
“Selfish mining is an instance of game-theoretic attacks that take advantage of information asymmetry in distributed systems. Such attacks tend to be subtle, unexpected, and at times, counterintuitive.”
Paper: https://www.cs.cornell.edu/~kevinnegy/Selfish%20Mining%20Re-Examined.pdf
Picture of abstract:
The Impact of Selfish Mining on Bitcoin Network Performance (2021)
Key passage: “block withholding delay and block withholding attacks degrade network performance…by increasing the probability of forking in the network, which harms the network but also opens the avenue for double-spending and other security attacks”
Picture of abstract:
Selfish & Opaque Transaction Ordering in the Bitcoin Blockchain: The Case for Chain Neutrality (2021)
Key passage: “Multiple large mining pools tend to selfishly prioritize transactions in which they have a vested interest; e.g., transactions in which payments are made from or to wallets owned by the mining pool operators.”
Paper: https://dl.acm.org/doi/pdf/10.1145/3487552.3487823
Picture of abstract: